Translation: Principles and Criteria from China’s Draft Privacy Impact Assessment Guide
In China’s emerging data protection regime, a call to systematically consider risks to personal information
Blog Post

Sept. 13, 2018
On June 13, China’s official information security standards organization, known as TC260, released for comment a draft guide for organizations to assess the privacy implications of a wide variety of practices. The guide—officially named Information Security Technology – Security Impact Assessment Guide of Personal Information (信息安全技术 个人信息安全影响评估指南)—is designed to set a Chinese standard for “privacy impact assessments” (PIAs), following a global trend of emerging procedures to identify and minimize risks to privacy.
PIAs generally come into play in scenarios where data processing poses high or unknown risks to privacy, for example when new products or practices in an organization trigger particular privacy concerns, or when large amounts of sensitive personal information will be processed. China’s new draft guide specifically addresses both private sector and government actors.
Once finalized, the guide would be formally non-binding, but—like many TC260 standards—would effectively establish standard practices and a basis for regulatory enforcement. Along with the Guide for De-Identifying Personal Information and Guidelines for Data Cross-border Transfer Security Assessment, both currently in the drafting stage, the PIA guide is designed to establish a tripartite standard system for personal information security under the broader Personal Information Security Specification, which is already in effect.
The guide covers details like who should initiate and lead PIAs (section 4.4), how to prepare (section 5.2), what factors should be considered with what weights (sections 5.4–5.6), and when PIAs should be conducted (section 6). In many aspects, the guide appears similar to an EU approach, setting a high bar to protect individual rights against data breaches. In the suggested criteria, heavy weight is placed on potential risks to individual interests, which range broadly from financial loss, and effects on credit scores, to discrimination, reputational damage, and psychological effects.
The guide embeds the idea of privacy-by-design, echoing elements of the EU’s General Data Protection Regulation (GDPR). It suggests that organizations assess impacts from the very beginning of a new product design and continue in an ongoing process whenever a significant legal or business environmental change occurs. Section 6.3 lists nine high-risk scenarios where impact assessments are suggested, which are highly similar to the list recommended by the EU advisory body WP29 in its Guidelines on Data Protection Impact Assessment supporting the GDPR.
Below is a translation of a crucial appendix to the draft PIA guide that elaborates the details regarding risks, practices, and standards for organizations to determine impacts on personal information security.
TRANSLATION
Appendix A: “Reference Method for Personal Information Security Impact Assessment” from “Information Security Technology – Security Impact Assessment Guide of Personal Information (Draft for Comment)”
A.1 – Assessing Impact on Data Subjects’ Rights and Interests
Impact assessment on data subjects’ rights and interests can be qualitative, quantitative, and semi-quantitative. The principles are listed in the following chart.
Chart A.1 – Principles for Assessing Impact on Data Subjects’ Rights and Interests
| Impact Description | Degree of Impact |
|---|---|
| Data subjects may suffer major, irrevocable, and insurmountable impacts, including unmanageable debt, incapacity for work, long-term mental or physical illnesses, death, etc. | Serious |
| Data subjects may suffer major impacts that are hard to surmount and/or would entail great costs to reverse, including fraud, money misappropriation, bank blacklisting, credit rating damage, reputational damage, discrimination, unemployment, judicial summons or subpoena, health deterioration, etc. | High |
| Data subjects may suffer serious impacts that are comparatively difficult to surmount, including extra cost, inability to use services, misunderstanding, fear and nervousness, minor physical illnesses, etc. | Middle |
| Data subjects may suffer certain levels of impact that can be surmounted, including extra time cost, nuisance, feelings of weariness and annoyance, etc. | Low |
Qualitative assessment, for example, can be conducted according to the Principles in Chart A.1 and be based on four dimensions: (1) influencing personal self-determination rights, (2) causing differential treatment, (3) causing personal reputational damages and mental stress, and (4) damaging personal property. The degree of these impacts can be divided into four levels—“serious,” “high,” “middle,” and “low”—according to the criteria in the following chart.
Chart A.2 – Judgment Criteria for Impact Assessment
Influencing personal self-determination rights
| Principles of Impact Assessment | Impact Description | Degree of Impact |
|---|---|---|
| Data subjects may suffer major, irrevocable, and possibly insurmountable impacts. | E.g., physical liberty limitation, bodily injury. | Serious |
| Data subjects may suffer major impacts that are hard to surmount and/or would entail great costs to reverse. | E.g., being forced to do things against personal will, being manipulated in value judgment decisions by intentionally instilled information, the possibility of limited physical liberty or bodily injury. | High |
| Data subjects may suffer serious impacts that are comparatively difficult to surmount. | E.g., lack of relevant knowledge or channels to correct personal information, extra cost to use products or services. | Middle |
| Data subjects may suffer certain levels of impacts that can be surmounted. | E.g., extra time costs. | Low |
Causing differential treatment
| Principles of Impact Assessment | Impact Description | Degree of Impact |
|---|---|---|
| Data subjects may suffer major, irrevocable, and possibly insurmountable impacts. | E.g., causing unemployment due to discrimination caused by information leakage. | Serious |
| Data subjects may suffer major impacts that are hard to surmount and/or would entail great costs to reverse. | E.g., causing discriminatory treatment related to personal legal rights, or damaging people’s fair-trade rights (inability to use all or portions of products or services). | High |
| Data subjects may suffer serious impacts that are comparatively difficult to surmount. | E.g., misunderstanding, or extra costs (including money, time, etc.) to use products or services. | Middle |
| Data subjects may suffer certain levels of impact that can be surmounted. | E.g., nuisance or weariness and annoyance, etc. | Low |
Causing personal reputational damage and mental stress
| Principles of Impact Assessment | Impact Description | Degree of Impact |
|---|---|---|
| Data subjects may suffer major, irrevocable, and possibly insurmountable impact. | E.g., reputational damage leaving the person incapable of earning income for a long time, long-term mental or physical illness such that the person can no longer work, death, etc. | Serious |
| Data subjects may suffer major impacts that are hard to surmount and/or would entail great costs to reverse. | E.g., reputational damage causing the person to lose their job, irreversible mental or physical illness, etc. | High |
| Data subjects may suffer serious impacts that are comparatively difficult to surmount. | E.g., causing misunderstandings, reputational damage (that can be fully or partially reversed through clarification), fear and nervousness, mental or physical illness (that can be cured within a short period), etc. | Middle |
| Data subjects may suffer certain levels of impacts that can be surmounted. | E.g., frequent nuisance, weariness and annoyance, etc. | Low |
Damage to personal property
| Principles of Impact Assessment | Impact Description | Degree of Impact |
|---|---|---|
| Data subjects may suffer major, irrevocable, and possibly insurmountable impact. | E.g., causing unmanageable debt, etc. | Serious |
| Data subjects may suffer major impacts that are hard to surmount and/or would entail great costs to reverse. | E.g., fraud, money misappropriation, credit damage, etc. | High |
| Data subjects may suffer serious impacts that are comparatively difficult to surmount. | E.g., social credit damage causing extra costs for financial products or services, etc. | Middle |
| Data subjects may suffer certain levels of impacts that can be surmounted. | Such as, extra procedures (or providing extra evidentiary documents) to correct personal information, etc. | Low |
The assessment process can start from the degree of impact on a specific data subject, and the degree of impact can be adjusted by referring to the following chart based on elements like the features of the data processing and/or of the group.
Chart A.2 – Adjustment Criteria for Impact Assessment
| Degree of Impact Before Adjustment | Conditions for Adjustment | Adjusted Degree of Impact |
|---|---|---|
| Serious | None | None |
| High | Personal data processing activity involves sensitive personal information, and the number of impacted data subjects exceeds 100,000. | Serious |
| High | The number of the data subjects impacted by personal information processing exceeds 5,000,000. | Serious |
| High | The impacted data subjects as a group have problems like low financial risk resistance capability or vulnerable mental capacity, e.g. juveniles, students, elderly people, etc. | Serious |
| High | Other uncontrollable factors, such as volatile local laws and policies in locations where data are stored after a cross-border data transfer. | Serious |
| Middle | Personal data processing activity involves sensitive personal information, and the number of the impacted data subjects exceeds 5,000,000. | Serious |
| Middle | Personal data processing activity involves sensitive personal information, and the number of the impacted data subjects exceeds 100,000. | High |
| Middle | The number of the data subjects impacted by personal data processing exceeds 5,000,000. | High |
| Middle | The impacted data subjects as a group have problems like low financial risk resistance capability or vulnerable mental capacity, e.g., juveniles, students, elderly people, etc. | High |
| Middle | Other uncontrollable factors, such as volatile local laws and policies in locations where data are stored after a cross-border data transfer. | High |
| Low | The number of data subjects impacted by personal data processing exceeds 5,000,000. | Middle |
| Low | Overly frequent disturbance to data subjects. | Middle |
In quantitative or semi-quantitative assessments, for example, an assessment can be conducted according to the costs paid by data controllers for damaging data subject’s interests. These costs usually include: violation costs (e.g., regulatory penalties, litigation costs, correction costs), direct business losses (e.g., decreased business income due to losing clients), reputational damages (e.g., damage to a brand, losing client’s trust), internal company culture damages (e.g., damaged business execution capability, losing staff morale due to value conflicts), etc.
A.2 – Assessing the Likelihood of Security Incidents
Assessments of the likelihood of security incidents can be qualitative, quantitative, and semi-quantitative. The principles are in the following chart.
Chart A.3 – Principles for Assessing the Likelihood of Security Incidents
| Likelihood Description | Likelihood |
|---|---|
| Adopted measures are seriously insufficient. Personal information processing activities are highly arbitrary. Security incidents are almost inevitable. | Very high |
| Adopted measures are insufficient. Personal information processing activities are arbitrary. Security incidents have happened or have been confirmed in a similar scenario. | High |
| Certain measures have been adopted. Personal information processing activities have followed basic standard principles. Security incidents have been confirmed in the same industry or field. | Middle |
| Comparatively effective measures have been adopted. Personal information processing activities have followed the standard best practices. Security incidents have not been confirmed yet. | Low |
In qualitative assessment, for example, security incident likelihood assessment can be conducted according to the Principles in Chart A.3 and based on aspects like “cyber environment and technological measures,” “standardization of process flow,” “participating staff and third parties,” “security situation and scale of processing,” etc. The likelihood can be divided into four levels—“very high,” “high,” “middle,” and “low”—according to the criteria in the following chart.
Chart A.4 – Judgment Criteria for Likelihood Assessment
| Likelihood Description | Likelihood |
|---|---|
| Interactions exist among the network environment, the internet, and massive information systems, and basically no security measures have been adopted to protect personal information. | Very high |
| Personal information processing is a normal and continual business activity that has (negatively) impacted the data subject’s interests or been the subject of heavy complaints, receiving public attention. | Very high |
| Anyone can access the personal information, no scope restraints exist on third parties to process personal information, or there have been cases of third parties misusing personal information. | Very high |
| Relevant security incidents induced by a threat have already been detected by the organization, or the organization has received relevant risk alert from supervision authorities. | Very high |
| Many interactions exist among the network environment, the internet, and other information systems, and the adopted security measures are insufficient. | High |
| Personal information processing is a normal and continual business activity, personal information processing is arbitrary, and there have been relevant complaints. | High |
| Loose staff management on personal information processing, and there are no relevant requirements to limit the scope of third-party personal information processing. | High |
| Relevant security incidents induced by a threat have already occurred within the organization or to a cooperating partner, the organization has received a relevant risk alert from authorities, or the number of the impacted data subjects is over 10,000,000. | High |
| Interactions exist among the network environment, the internet, and other information systems, and certain security measures have been adopted. | Middle |
| Personal information processing is a normal business activity, personal information processing lacks standardization, and the cooperative partners or other organizations in the same field have received relevant complaints. | Middle |
| There are staff management mechanisms and restraints imposed on the scope of third-party personal information processing, but the effectiveness of the management and supervision is unclear. | Middle |
| Relevant security incidents induced by a threat have been detected by other organizations in the same field or confirmed by relevant reports of professional organizations, or the number of the impacted data subjects is over 1,000,000. | Middle |
| The network environment is comparatively independent without many interactions, and effective measures have been adopted to protect personal information security. | Low |
| Personal information processing is not a normal business activity, personal information processing is standardized, and there are few complaints against this activity. | Low |
| Staff management and review is comparatively strict, and there are effective restrictive conditions with supervision on the cooperation with third-parties. | Low |
| The security incidents induced by a threat have only been predicted by professional organizations. | Low |
The assessment process can start from the the nature of the incident itself and the empirical data and then the level of likelihood can be adjusted based on the data controllers’ tailored security measures and other relevant experiences. The adjustment criteria can refer to the following chart.
Chart A.4 – Adjustment Criteria for Likelihood Assessment
| Likelihood Before Adjustment | Conditions for Adjustment | Adjusted Likelihood |
|---|---|---|
| Very high | Experience in handling relevant complaints is present, and data subject acceptance has been obtained. | High/Middle |
| Very High | Effective security measurements tailored to the features of the security incidents have been implemented in advance, or security safeguards have been improved in a timely manner according to security alerts. | High/Middle |
| High | Experience handling relevant complaints is present, and data subject acceptance has been obtained. | Middle |
| High | Effective security measurements tailored to the features of the security incidents have been implemented in advance, or security safeguards have been improved in a timely manner according to security alerts. | Middle |
| Middle | Solutions for relevant complaints have been implemented. | Low |
| Middle | Effective security measurements tailored to the features of the security incidents have been implemented in advance. | Low |
| Low | None | None |
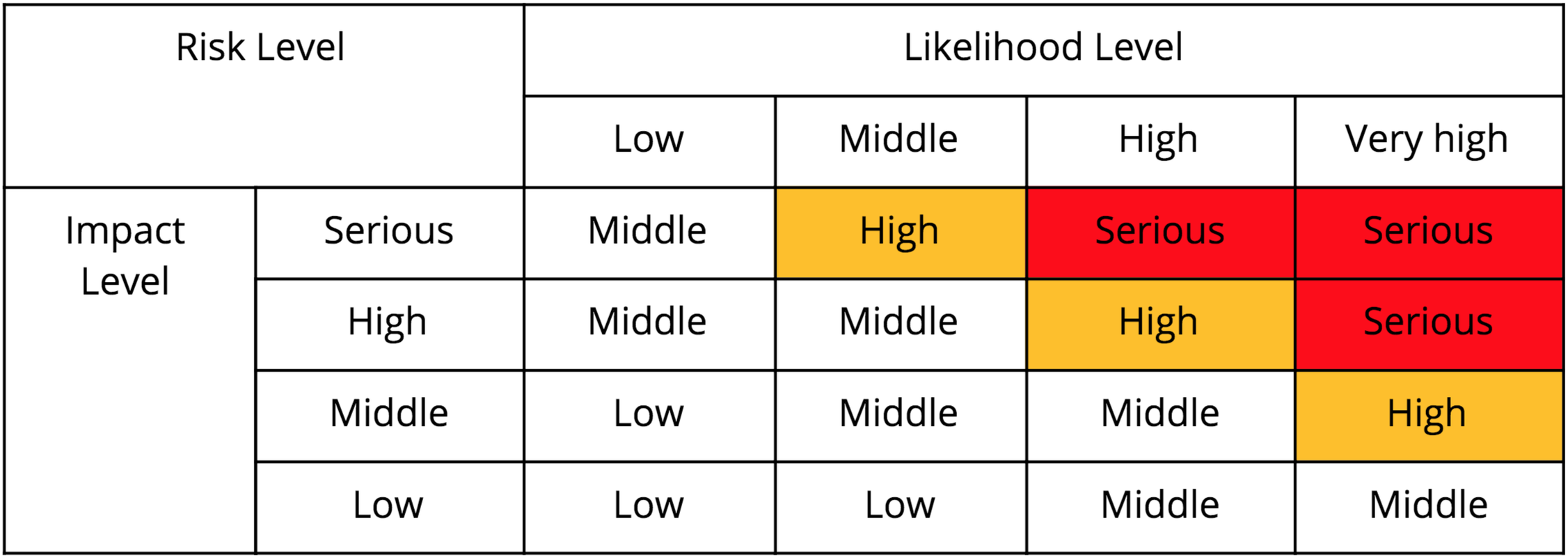
A.3 – Comprehensive Assessment of Personal Information Security Risks
Based on a comprehensive analysis of the two elements—impacts on data subjects’ interests, and likelihood of security incidents—the risk level can be assessed with relevant improvement suggestions to form a final assessment report. The risks can be divided into four levels: serious, high, middle, and low. For example, for qualitative assessment, the following chart serves as a reference.
Chart A.5 – Risk Level Judgment Chart